What is Rootkit.boot.Harbinger.a
Rootkit.boot.Harbinger.a is a Trojan horse that gets on users’ computers and will cause great damage to computers. This is a big threat to users as it can offer convenience for people who developed it and make them easy to access to compromised computer. And if they hack into you’re a compromised computer, they could get control of it and doing everything on compromised computers, such as collecting your highly confidential data, record your online activity. Besides, as a Trojan, Rootkit.boot.Harbinger.a can incur many other threats like webcake 3.0 or other viruses that could pose a great risk to your computer.
How could Rootkit.boot.Harbinger.a get on your computer? Try to think about what you have done with your computer. Did you ever visit insecure sites, like gamble sites or porn sites? If you did, then this can explain why your computer got infected because those sites contain many virus like Rootkit.boot.Harbinger.a which might appear as pop ups or other ads you are apt to turn it down or click it out of curiosity. If you visit, click ads or pop-ups or other links, then you have much great possibility of being infected. Also be careful with those free programs, because this virus’ code can be embedded with those compromised programs. And third possible way may be that you have infected with other virus and that virus gets your computer infected with this virus.
But no matter in which way you get infected, removing it is what you need to do before Rootkit.boot.Harbinger.a do more harm to your computer.
Here are some damages that comes along with Rootkit.boot.Harbinger.a:
1: After being infiltrated, your computer, will be exposed to hackers. Your other files and data will lose or being copied.
2: Rootkit.boot.Harbinger.a can change your system’s setting and modify registry, which make it stay legally in your computer.
3: With your system’s setting being changed, Rootkit.boot.Harbinger.a can compromise your computer and make your computer more vulnerable to attack.
4: Rootkit.boot.Harbinger.a get on victims’ computers with other virus like delta serach,dirty decrypt, webcake or other viruses.
How to Remove Rootkit.boot.Harbinger.a
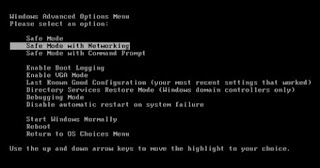
Following this post and you will learn how to remove the Rootkit.boot.Harbinger.a. Before we move forward, you need to restart your computer and enter the Safe Mode with Networking. Boot up the computer, press F8 at the very beginning and then choose “Safe Mode with Networking” and press Enter to get in the Safe Mode with Networking.
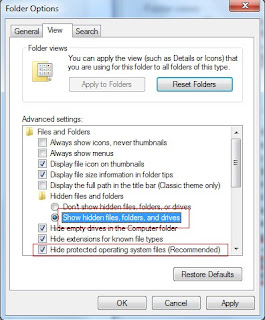
Step 1: Show all the hidden files
Click Start>Control Panel>Appearance and Personalization>Folder Option>View.
Under the tab "View", choose Show hidden files, folders and drivers.
Step 2: End the related process.
Launch the Task Manager and end Random.exe
Step 3: Enter the registry.
Press"Win+R" and then type "regedit" and hit "Enter" to enter the registry editor.
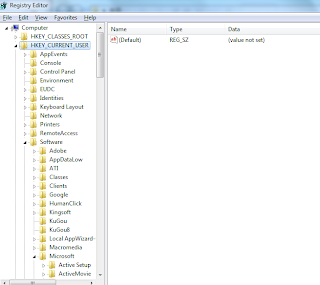
Find these regsitry entries and delete them all:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “[RANDOM]”
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Random “.exe”
Note: If you have any difficulty during the removal process, please feel free to contact us anytime by starting a live chat with us from here: