What is zero access.TH?
zero access.TH is a Trojan horse that can sneak into your computer and cause damage to your system. This virus originated from Trojan Zero Access family and different from oher family members like Trojan Zero Access.c. AS a Trojan, it was embedded malicious code and was programmed to do evil things. What can they do? Here you will learn more of it.
It is designed in tiny size so that it can easily avoid being detected and being deleted by antivirus. After successfully infiltrated your system and survive the detection of antivirus, trojan Zero Access can open the backdoor of your system and then provide attackers with much great convenience to access your computer. That’s its main purpose. Then hackers can hack into your system, do whatever they want. They can control your system and use it to attack others, they can copy your files stored on your hard drive, and they can do experiment on your computer by dropping various viruses on your system. Besides, zero access.TH can incur other threats like webcake. Apart from those, zero access.TH can change your registry, adding some useless values to the registry and making computer runs slower than before.
How to prevent it?
It can be distributed by spam Emails, so next time when you open a spam Email, do not click its attachment because those attachments are bundled with zero access.TH. Also, when you download programs, be careful with those unsafe websites. zero access.TH can be bundled with those programs and if you choose to install it in default way, you are more likely to catch it, so what you need to do is install it step by step and uncheck those redundant options that have no relations with normal program. The last thing you should know is that do not go to the insecure sites, like porn sites. These websites loaded with pop ups or ads and if you click it(even though you choose to close the pop-up), it will automatically install in your system. If you unfortunately infected with zero access.TH, such an annoying virus, do not freak, we will offer you the most effective way to remove zero access.TH.removal Instruction:
Removal instruction 1: Download Malwarebytes to remove zero access.TH
Download Malwarebytes to scan and delete it. You can go to the Malwarebyte official websites and download it remove. But normal antivirus could not completely remove zero access.TH, something like redundant registry values and corrupted system files still stay in the system, so here we offer second way: manually removal instruction.Removal instruction 2: Manually remove zero access.TH
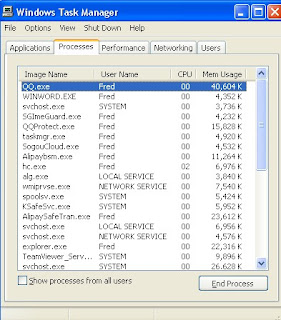
Step 1: Go to the Task Manager and then end the process of zero access.THHit Crtl+Shift+Esc to launch the Task Manager and then find Random.exe and end it.
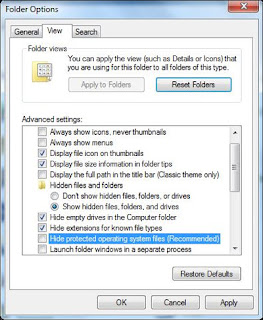
Step 2: Show hidden files.
Click Start>Control Panel>Appearance and Personalization>Folder Option>Show hidden files, folders, and drives>>Ok.
Step 3: Go to the registry editor and then delete useless registry values.
Press”Win+R” and type “regedit” in the dialog box, hit Enter.
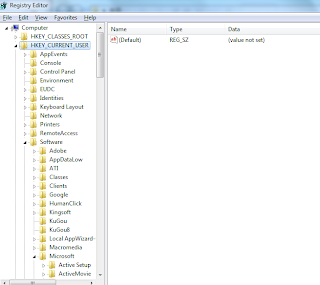
Find following registry entries and then delete them:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\[RANDOM CHARACTERS].exe
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run ‘Random’
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Random
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “CertificateRevocation” =Random
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\run\Random.exe
Find following corrupted files in your C drive and remove them all:
%AllUsersProfile%\random.exe
%AppData%\Roaming\Microsoft\Windows\Templates\random.exe
%Temp%\random.exe
%AllUsersProfile%\Application Data\random
%AllUsersProfile%\Application Data\~random
NOTE:If have any problem during the removal process, please feel free to contact here to get professional online tech support.



No comments:
Post a Comment